The botnet attacking Electrum has grown to 152,000 contaminated computer systems and has now stolen $4.6 million in cryptocurrencies comparable to Bitcoin, in line with Malwarebytes.
Malwarebytes states that it has been “closely monitoring” the assault in opposition to the Electrum Bitcoin pockets.
The corporate states how the botnet got here to fruition, stating:
“Victims were being tricked to download a fraudulent update that stole their cryptocurrencies,” defined Malwarebytes.
In a while, the risk actors launched a Distributed Denial of Service (DDoS) assaults in response to Electrum builders making an attempt to guard their customers.
As Bitcoinist first reported on the botnet in December final 12 months, the quantity stolen stood at USD $900,000. The phishing try’s first iteration got here as a “security update” however would later evolve because the rip-off turned extra complicated.
The safety replace window beneath is brought on by the trojan which is a part of the botnet.
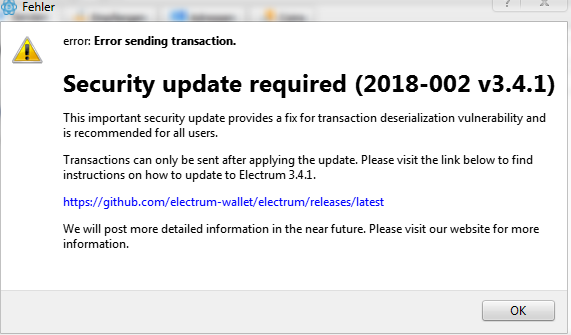
The botnet attacking Electrum is rising
“On April 24th, the variety of contaminated computer systems was beneath 100,000. Then the day after, “the variety of contaminated computer systems would peak at 152,000, wrote Malwarebytes.
The botnet’s dimension will be tracked with this on-line device right here.
New botnet “loader” recognized
Malwarebytes provides {that a} second botnet loader has been recognized as “Trojan.BeamWinHTTP” that downloads the trojan “transactionservices.exe” — which is the primary contaminated file that seeds the botnet.
The primary loader was detected as “ElectrumDosMiner.”
Visualizations of the dimensions of the botnets was additionally supplied by Malwarebytes.
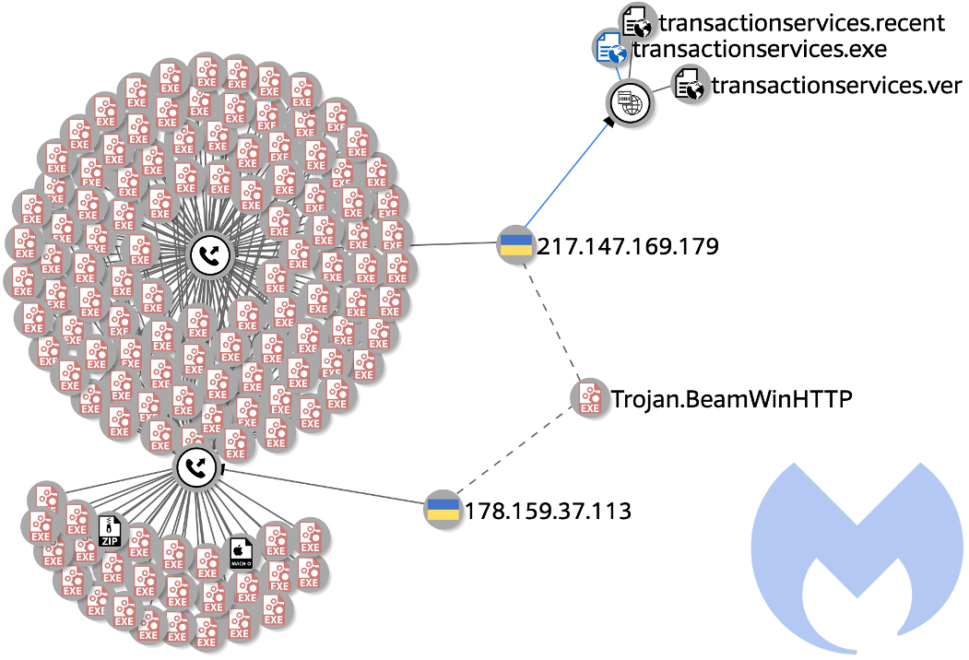
The second image beneath reveals the depth of the botnets structure in addition to its complexity.
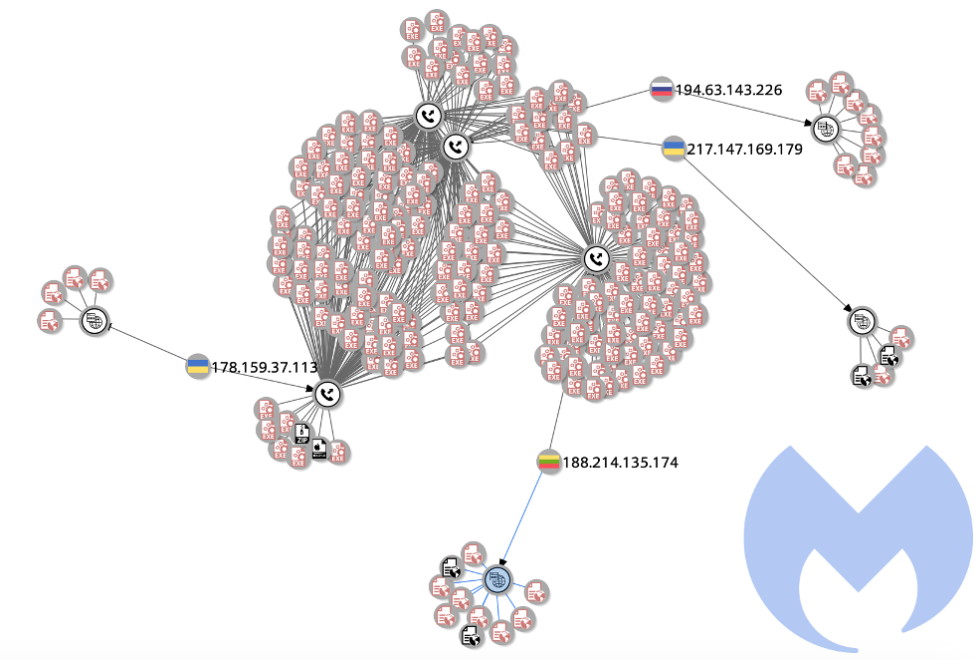
Assaults since late December 2018
In an in depth weblog put up, on the topic, Malwarebytes claims that the assaults have occurred in opposition to the community since 2018 earlier than rising sharply in 2019.
As retaliation for making an attempt to repair the corporate’s personal software program, the criminals launched a denial of service assault in opposition to Electrum’s servers. The attackers had been additionally in a position to reverse an preliminary patch by the corporate by redirecting customers to compromised machines that contained the malware.
Generally known as being a “lightweight” pockets, Electrum was chosen for assault resulting from its simplified structure, working in a shopper/server configuration. It was this configuration that will finally enable attackers to compromise the community’s safety.
Particularly, attackers took benefit of the truth that anybody might function on the community as a public Electrum peer. Attackers then launched what’s known as a Sybil assault that introduces compromised nodes into the community. The results of such an assault was that lots of of 1000’s of computer systems have been compromised by the false safety replace and different means proven at the beginning of this text.
The put up Electrum Botnet Steals $4.6 Million in Bitcoin, Cryptocurrencies appeared first on Bitcoinist.com.

















